It is time for a change!
The amount of data breaches with massive impact is continously growing. Breaches at enterprises like Facebook, Twitter or Marriott alone did lead to hundreds of millions of data records compromised.

Unfortunately, this is but one of many threats!

Harness the technology of the future today
Raise safety awareness
Protect your investment
Open up new business opportunities
All involved parties agreed that it must be possible to find a truly safe – and therefore, completely novel – way to secure our data.
This technology is considered a secure solution for our networked future.
No matter which industry or IT-related field, whether it is the Cloud, IoT (Internet of Things), smart devices or autonomous driving – data has never been so valuable and yet as vulnerable as today.
It‘s time to change the game!

NVD Technology
You cannot touch NVD technology, you cannot put it into simple words and you cannot see it, but: NVD is an essential factor to solve the problems we described to the left!
We will take the time to explain this technology of the future to you.Don’t miss out on the eye-opening experience of discovering the game changer in data security technology!
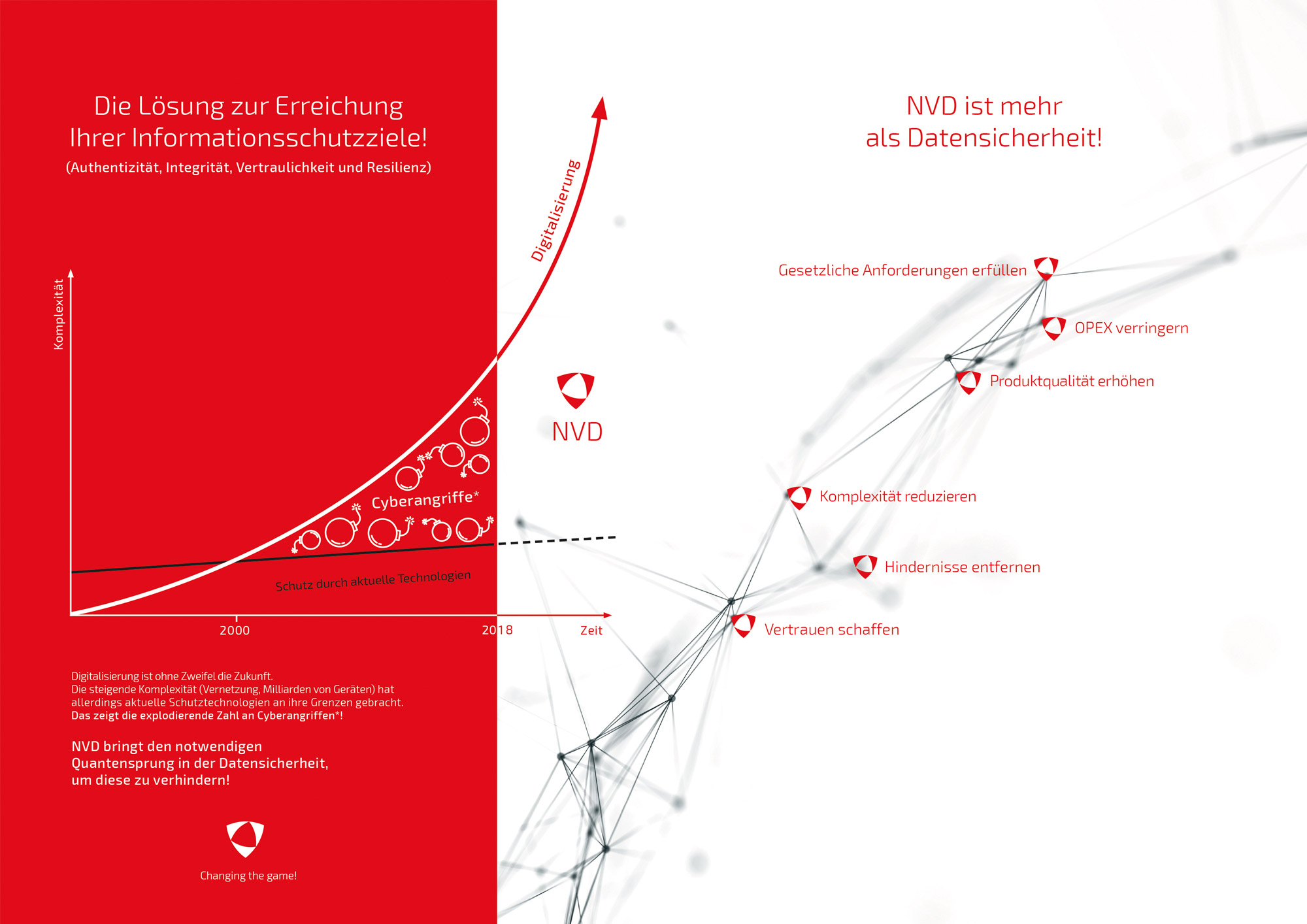
The solution to reach your information protection goals
(authenticity, integrity, privacy and resiliency)

Cyberattacks!!
Digitization is the future without any doubt.
However, the increasing complexity (networking, billions of devices) has pushed current protection technologies to their limits, and as a result the number of cyberattacks have increased dramatically!
NVD leads to the necessary
quantum leap in data security
to prevent those!
NVD is more than data security!
NVD lifts products and applications to a new quality level, generates confidence and fulfils legal requirements – with reduced complexity and OPEX.
While debating the future …
The digital world is living in the middle ages!
Current technologies build protections AROUND data!
Problems
1
Loss of control
As soon as you share data, you lose control over what happens to it next. There is no way to actively withdraw data privileges afterwards.
2
Insufficient protection
Building protection around data using encryption or encapsulation is the wrong strategy, because data needs to be unencrypted to be processed – which means protection must be removed beforehand.
3
Non-compliant
Not only your data, but in particular, additional information (meta data) is critical, since analytical systems can process this info, potentially identifying personal info associated with this data.
4
Complexity
An increasing number of devices and the need to securely connect them escalates complexity (key management), weakening security. Current technologies are doomed to lead into an impasse!
You can’t attack data you can’t see.
This is what the future looks like!

NVD integrates protection INTO the data as it is created!
Solutions
1
Control
2
Digital immunity
We integrate protection and privacy directly into your data, making them immune to attacks and manipulation. Even insider attacks or compromised systems cannot harm them.
3
Compliance
We remove all personally identifiable information, which eases to comply with today’s and tomorrow’s legal requirements.
NVD does not contain any metadata and no personally identifiable information. Therefore NVD protected data ensures privacy, for what you can’t see can’t be stolen or manipulated.
4
Scalability
Efficient protection is applied right as the data is generated, providing uniform protection for anything, whether it is a smart electricity meter or a full-fledged industrial plant.
1
Control
NVD puts you back in control of your data!

You alone decide who will have access to your data and you will never surrender control over it! You will always have the option of withdrawing access information retroactively.

Classical protection- and access control systems are outdated. We created solutions which integrate the protection into the data and make todays log in procedures obsolete. Known attack vectors become unusable and data authenticity, integrity, privacy and resiliency are provided by design.
Remaining in control is very costly or almost impossible – or do you know what happend with your shared data?

Your advantage with NVD
Re-gain control of your data! You retain exclusive control over your own data! You decide about access and viewing privileges!

Disadvantage without NVD
No control over your data whatsoever! Others are in charge!
2
Digital Immunity
Integrated protection inside the data, eliminated weak points: This is digital immunity.

Data manipulation and data theft are no longer possible, not even with quantum computers. Your data content is immune to cyberattacks, right away, and more importantly, in the future.

Keys, locks, and gates have been common points of attack for centuries. As our computer systems become more powerful, these obstacles are ever easier to overcome. Integrated protection and privacy inside the data ensure your immunity.

Your advantage with NVD

Disadvantage without NVD
3
Compliance
We remove all personally identifiable information, which makes us compliant with today’s and tomorrow’s legal requirements.

NVD does not contain any metadata and no personally identifiable information. You don’t have to worry about any legal restrictions in terms of privacy, for what you can’t see can’t be stolen or manipulated.

Metadata and especially personal information provide excellent cues for attackers to find weak spots. NVD does not use any meta data at all and ensures compliance.

Your advantage with NVD

Disadvantage without NVD
4
Scalability
We don’t have a weak link. Seamless data protection from the very start.

Plug-and-play, easy-to-use privacy for any device. For us, security and performance are both must-haves to give IoT solutions the security and performance they need to boost innovative business models.

Billions of devices will be communicating and sharing data in the IoT, without sufficient protection. We establish perfect end-to-end protection, without increasing the effort, regardless of application or device.

Your advantage with NVD

Disadvantage without NVD
Expert proven
Not only secure, but truly unique. Various experts confirmed the innovations of NVD technology, also reflected in our awards and patents.


Today’s data security technologies are already reaching their limits and in no way meet the requirements of autonomous driving, the IoT or the healthcare sector!

Your advantage with NVD

Disadvantage without NVD
The Decision-Makers’ Top Concerns
according to Gartner’s CIO agenda
4 exemplary fields of application

Internet of Things
Industrial Cloud, SmartGrid, Connected-/Autonomous Cars
Issues
Rising complexity makes it virtually impossible to control and secure all connected devices.
Wie kann man die Flut dieser wertvollen Daten/Informationen kontrollieren?
Und wie kann man ausschließen, dass Informationen manipuliert werden?
Mit heutigen Sicherheitslösungen sind diese Herausforderungen nicht zu lösen!
Solutions
Example CarSharing

Healthcare
Legally compliant, Electronic patient files
Issues
It is currently virtually impossible to ensure legally compliant long-term storage of complete data and conduct a targeted analysis of this data at a later point in time.
Eine rechtskonforme langfristige Speicherung der kompletten Daten und zielgerichtete Auswertung auch zu späteren Zeitpunkten ist derzeit rechtlich nahezu unmöglich.
Solutions
Of course, additional protections such as (partial) anonymization can be implemented as well, but they do not affect the original raw data – and thanks to NVD, even this newly generated anonymized data can only be used in a targeted fashion.
abgestimmten Nutzungsbereiches oder nach der Nutzungsdauer wird durch das NVD Zugriffsverfahren verhindert, da die Daten nicht auffindbar wären.
Natürlich können zusätzliche Schutzmechanismen, wie beispielsweise eine (Teil-)Anonymisierung genutzt werden, davon sind aber die ursprünglichen Roh-Daten nicht betroffen – und selbst diese neu generierten anonymisierten Daten könnten durch NVD wieder nur zielgerichtet genutzt werden.
Example Electronic patient files

Financial services providers / FinTechs
Data control and new, data-based business models
Issues
In addition, new regulations such as PSD2 require these old systems to open up so financial institutions can share customer information. This leads to the aforementioned loss of control over a precious banking asset – their data.
Solutions
Legal requirements are met without the dreaded loss of control. This raises whole new cost-saving potentials and opportunities for new business models in the area of data trade – as Amazon, Facebook and Google are already doing with great success.
Es werden also die gesetzlichen Verpflichtungen erfüllt, ohne den gefürchteten Kontrollverlust, und es ergeben sich vollkommen neue Einsparpotentiale und Geschäftsmodelle im Bereich des Datenhandels, wie es heute schon Amazon, Facebook und Google mit großem Erfolg praktizieren.
Example Banking Cloud

Cloud providers
Creating goodwill for Cloud providers
Issues
Today’s Cloud providers often circumvent encryption in order to be able to offer cheap B2C and B2B storage solutions. This is what makes space-saving deduplication possible in the first place.
Heutige Cloud-Anbieter umgehen häufig die Verschlüsselung, um kostengünstige Speicherlösungen dem B2C und B2B Markt anbieten zu können. Nur so ist heute die platzsparende Deduplizierung möglich.
Solutions
Also, NVD-protected data is stored de-duplicated on any server, globally and with high performance, fortifying your level of protection and greatly accelerating access speed.
Desweiteren werden die NVD-geschützten Daten von Anfang an dedupliziert auf beliebigen Servern, weltweit und performant abgelegt.
So steigern Sie Ihren Schutz, und die Zugriffsgeschwindigkeit wird extrem erhöht.
Beispiel Public wird zur Private Cloud
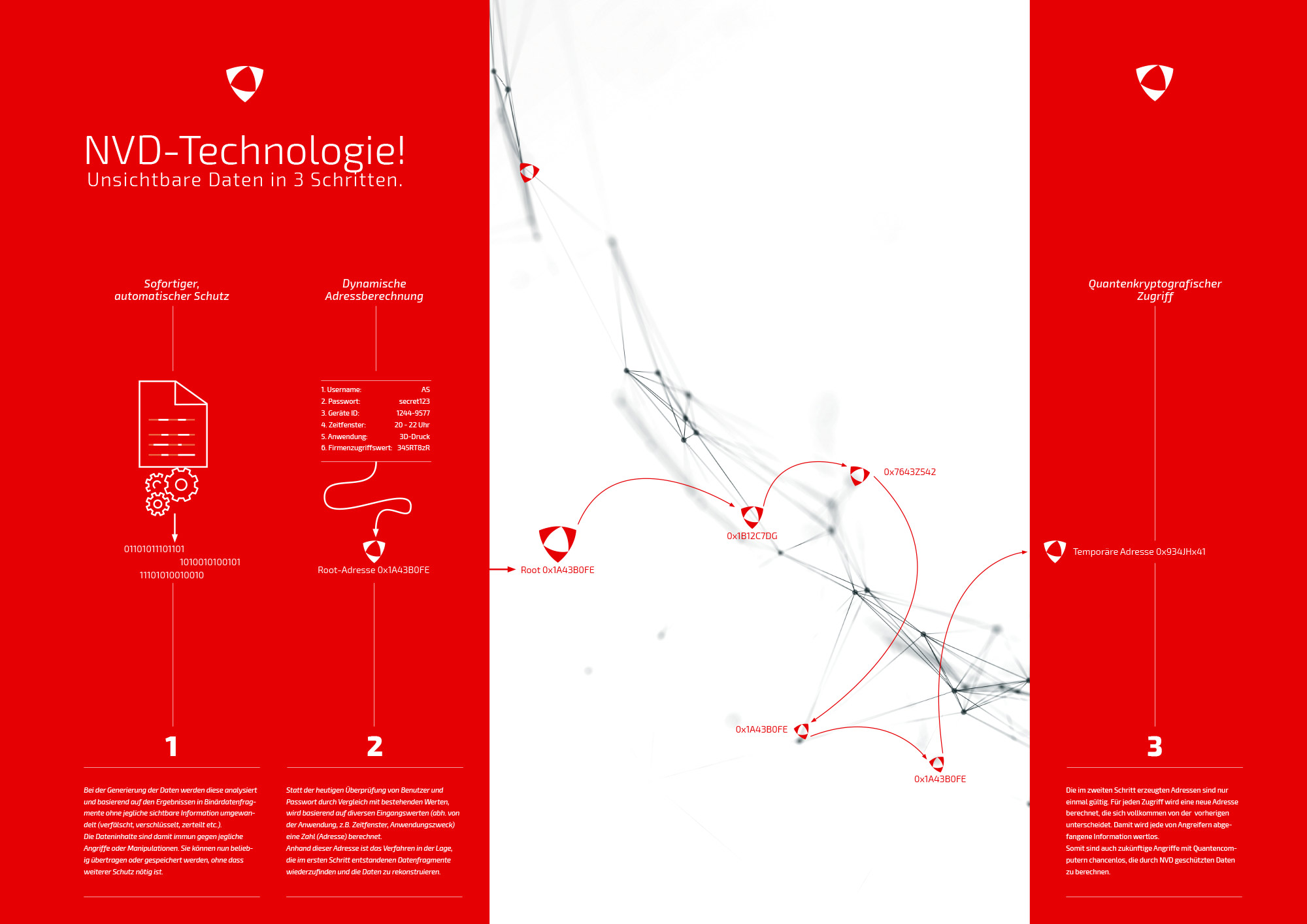
NVD-Technologie!
Invisible data in 3 steps
1
Immediate, automatic protection
As the data is generated, it is analyzed and, based on the results, converted into binary fragments without any visible information (distorted, encrypted, disjointed etc.). Data is thus immune to any attack or manipulation. It can now be transferred or stored at will, no further protection necessary.
2
Dynamic address calculation
Instead of verifying users and passwords based on existing information, as we do today, a number (address) is calculated based on various entry values that depend on the application, i.e. timeframe, purpose. Based on this address, the method can retrieve the data fragments generated in the first step and reconstruct the data.
3
Quantum-cryptographic access
The addresses generated in the second step are valid only one single time. Each access involves calculating a new address, which is completely different from the previous one. This makes any information that attackers may intercept utterly useless. This means even future attacks using quantum computers stand no chance of calculating NVD-protected data.
We are building the foundation for solutions of the future!
Mentioned enterprises benefit from NVD!
Safe
(autonomous) driving
Apple, BMW, Bosch, Continental, Daimler, Ford, GM, Google, Honda, Infineon, Tesla, Toyota, Uber, VW
Tamper-proof
Smart Grids
ABB, Deutsche Telekom, EON, Gazprom, GDF, Landis+Gyr, KEPCO, Schneider El., SGCC, SMA Solar, S&T
Burglary-proof
Smart Homes
Amazon, Apple, AT&T, GE, Deutsche Telekom, Google, Samsung, Siemens
Data
at your fingertips
AT&T, AWS, BT, China Mobile, EMC, Hitachi, IBM, Microsoft, NetApp, Telefonica, Telekom, Verizon, Vodafone
Replacing asymmetrical encryption
AMD, Apple, Broadcom, EMC, Foxconn, Google, IBM, Intel, Microsoft, Oracle, Qualcom, SAP
High-security
smartphones
Apple, BBK Electronics, China Mobile, Huawei, Lenovo, LG, Samsung, TCL/Alcatel, Xiaomi, ZTE
Anonymous
digital lockers
BNP Paribas, Credit Suisse, Deutsche Bank, HSBC, ICBC, JP Morgan Chase, Mitsubishi, Financial Group, UBS
Controlled data
trade/-rental
BNP Paribas, Credit Suisse, Deutsche Bank, HSBC, ICBC, JP Morgan Chase, Mitsubishi. Financial Group, UBS
Blockchain
Optimization
Google, IBM, Microsoft, Unilever, Visa, Walmart
Anonymous,
highsecurity collaboration
Government: Department of Defence, Homeland Security, Army
Tamper-proof and
anonymous voting systems
Governments
Cost-reduced
cyber insurance
Allianz, Axa, MetLife, Nippon Life Insurance, Ping an Insurance, Prudential




Safe (autonomous) driving
Tamper-proof Smart Grids
Burglary-proof Smart Homes
Data at your fingertips
Replacing asymmetrical encryption
High-security smartphones
Anonymous digital lockers
Controlled data trade/-rental
Blockchain Optimization
Anonymous, highsecurity collaboration
Tamper-proof and anonymous voting systems
Cost-reduced cyber insurance
Think like us
outside of the box!
Think BIG! Think NVD!